AWS Client VPN vs. OpenVPN
Note: Tennex does not receive any compensation from any products or companies referenced in this article.
This post is the first in a series discussing some foundational infrastructure areas in AWS, such as networking and access control. Today's topic - Virtual Private Networks (VPNs). A good strategy for remote ingress is a critical ingredient in your cloud strategy.
There are several methodologies you can use. The most common one I've come across over the years is a free-tier Amazon Linux server hosted in a public subnet running a free copy OpenVPN Access Server. In fact, I used this very method for years despite AWS launching a native alternative in 2018.
I always assumed that AWS Client VPN was too expensive. Mainly because, on the surface, at least, it is. However, AWS’s native AWS Client VPN may prove to be a better method at scale. I decided to model these two tools and compare them in three areas:
- Cost
- Ease of implementation
- Operational efficiency
Let's dive in.
OpenVPN vs. AWS Client VPN
OpenVPN has been around in the industry for a while and has several options for production-level deployments (including a SaaS model). In particular, the OpenVPN Access Server is a great tool that's quick to install and configure and free for up to 2 concurrent users. If you require more users, you can purchase a license.
AWS first introduced AWS Client VPN in December 2018. This native AWS tool attaches to your VPC via an AWS Client VPN Endpoint Association with an hourly charge and comes paired with a free client to install on your endpoint device (same as OpenVPN). Then, you're charged per connection/hour.
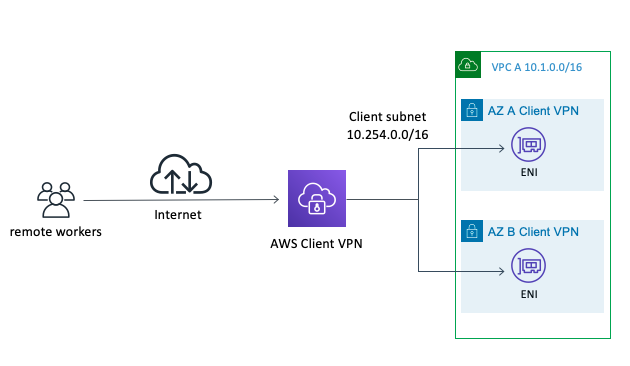 Image Credit: AWS
Image Credit: AWS
So, we have two tools, both alike in dignity. One is less expensive but requires a server, while the other is initially more expensive but native to AWS. Which one should you choose?
Round 1: Cost
The most obvious question to ask is one of cost. Pick the one that's less expensive, duh! The answer is a bit nuanced, though, and requires some analysis. Let's assume we have a team of 5 users who must connect to the VPN for 4 hours per day, 5 days per week (80 hours/month).
OpenVPN appears less expensive at first glance if your usage is low. With only 2 concurrent users, you'll be looking at:
- $0.0209/hr for 1 t3.small EC2 = $15.54/mo
-
$15.54/month
Compared to AWS Client VPN’s cost of:
- $0.10/hr for AWS Client VPN Endpoint Association = $74.40/mo
- $0.05/hr for 1 Connection * 4 hours/day * 2 users = $8/mo
-
$82.40/month
Wow!! OpenVPN is nearly 80% less expensive than AWS Client VPN as long as you only need 2 concurrent seats. Let’s look at the cost again for our team of 5:
- 5 users connect for 4 hr/day to OpenVPN
- $0.0209/hr for 1 t3.small = $15.54/mo
- $750/yr OpenVPN 10 seat license = $62.50
-
$78.04/mo
- 5 users connect for 4 hr/day w/ AWS ClientVPN
- $0.10/hr for endpoint = $74.40/mo
- $0.05/hr for connection * 4 hours/day * 5 users = $20/mo
-
$94.40/mo
That's much closer, only a 17% cost difference in favor of OpenVPN. The key here is scalability - as more users sign on, OpenVPN becomes less and less appealing due to the requirement for licensing (which is sold in highly inflexible packs). The chart below shows the extent of the damage.
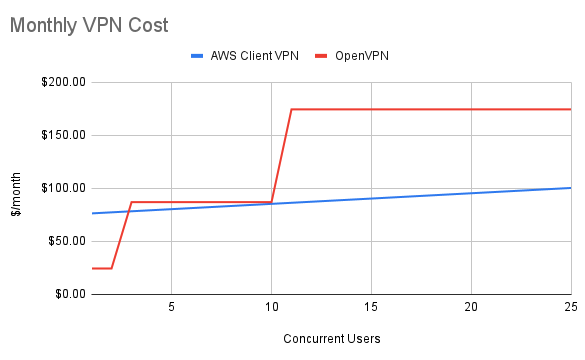 Monthly cost of OpenVPN and AWS Client VPN
Monthly cost of OpenVPN and AWS Client VPN
As you pass 10 users, the cost comparison heavily favors AWS Client VPN. However, it's important to remember that AWS Client VPN charges per subnet for its Endpoint Association. Depending on your network architecture, this may add costs. I'll give this round to OpenVPN because we're assuming we're working with a small team.
Advantage: OpenVPN
Round 2: Ease of Implementation
Keeping the same small team example, let's focus on implementation. OpenVPN is an application meant to run on a server. This means launching a full-blooded EC2 instance which immediately introduces some complications. I say "complications" because who needs another server to manage?
Remember, we're working with a small team here. In addition to simply existing, OpenVPN requires RADIUS for full federation with SSO (LDAP does have native support), which means, in all probability, that you've now got two servers to build and manage. OpenVPN supports MFA but requires additional configuration for a tool like Duo.
Alternatively, AWS Client VPN is an AWS platform tool and is extremely simple to launch and configure. Federating via SAML is part of the implementation process, and connecting to your existing VPC is a breeze. Well done, AWS.
Advantage: AWS Client VPN
Round 3: Operational Efficiency
Last but not least, let's explore Operational Efficiency (perhaps better thought of as "how often am I going to log into this thing to manage it?").
The arguments against launching more static infrastructure around scalability, configuration (cattle vs. pets), patching, and backups apply here en masse. Moreover, there's a licensing consideration. Remember, OpenVPN runs on a server. License files are installed locally, potentially creating a single point of failure. Recent additions like high-availability and portable licenses work to mollify us a bit, but there's no competing with a full platform service.
AWS Client VPN has no infrastructure to manage. That's the start and end of it. Some consideration should be given to network ingress management (e.g., Security Group and Route Table configuration), user management, etc., but you'd be on the hook for all of that with OpenVPN as well. AWS Client VPN will be simpler to manage long term, hands down.
Advantage: AWS Client VPN
Results - Winner: AWS Client VPN
And the winner is… AWS Client VPN!
Honestly, I didn't expect this result. For years I assumed AWS Client VPN was unreasonably expensive and, at the low end, it is more expensive than its direct competitor. However, as with most AWS platform services (looking at you, RDS), the slight premium paid for the service more than makes up for the gains in operational efficiency. And, at scale, AWS Client VPN becomes the more economical option anyway.
If you're looking at ingress options for your VPC, you should absolutely be considering AWS Client VPN. The cost scales well, there's little to no management overhead, and there are native integrations with your AWS account and SSO provider.
The Curveball - What about SSM?
What about AWS Systems Manager (SSM) Session Manager? Around the same time as the AWS Client VPN launch in 2018, AWS finally caught up to GCP by introducing a handy way to gain access to a shell via the console called Session Manager. AWS SSM Session Manager provides a secure tunnel (via API endpoints) directly tied to your IAM Principal and logged in CloudTrail and CloudWatch. Even cooler, you can access it from your local shell via some tricky SSH tunneling.
I'll leave you with an exciting thought, then - consider whether you need a VPN at all. We'll cover Session Manager in a future article. It's a fantastic tool to minimize or eliminate the need for a VPN.
As with all things AWS, it's worth it to challenge any long-held beliefs around traditional infrastructure configuration. If you're willing to push the envelope, you might find a simpler solution by going cloud-native.
About Tennex
Tennex is a born-in-the-cloud AWS consulting partner that simplifies the cloud journey for growing and established biotechnology companies. Leverage our comprehensive portfolio of infrastructure as code, automated workflows, proven delivery methodologies, and team of highly specialized AWS experts to simplify and accelerate your cloud journey. With practical guidance, Tennex enables businesses to adopt cloud more thoughtfully and grow more intentionally. To learn more, visit https://tennex.io - Cloud should be simpler, grow with us.
.png?width=1432&height=342&name=tennex%20Logo-E4-side-by-side%20(1).png)